How CPUs are Designed and Built
Nosotros all think of the CPU as the "brains" of a calculator, but what does that actually mean? What is going on inside with the billions of transistors to make your computer work? In this 4-part mini series we'll be focusing on computer hardware design, covering the ins and outs of what makes a computer work.
The series will encompass estimator architecture, processor circuit design, VLSI (very-large-scale integration), chip fabrication, and future trends in calculating. If you've always been interested in the details of how processors piece of work on the inside, stick around because this is what yous want to know to go started.
We'll start at a very high level of what a processor does and how the edifice blocks come together in a functioning blueprint. This includes processor cores, the memory bureaucracy, branch prediction, and more. Offset, we need a basic definition of what a CPU does. The simplest explanation is that a CPU follows a set of instructions to perform some operation on a gear up of inputs. For instance, this could be reading a value from memory, then adding it to another value, and finally storing the event back to memory in a different location. It could also be something more complex like dividing two numbers if the result of the previous calculation was greater than nil.
When you desire to run a plan like an operating system or a game, the plan itself is a series of instructions for the CPU to execute. These instructions are loaded from memory and on a simple processor, they are executed one by one until the program is finished. While software developers write their programs in loftier-level languages similar C++ or Python, for example, the processor can't empathise that. It merely understands 1s and 0s then we demand a manner to represent lawmaking in this format.
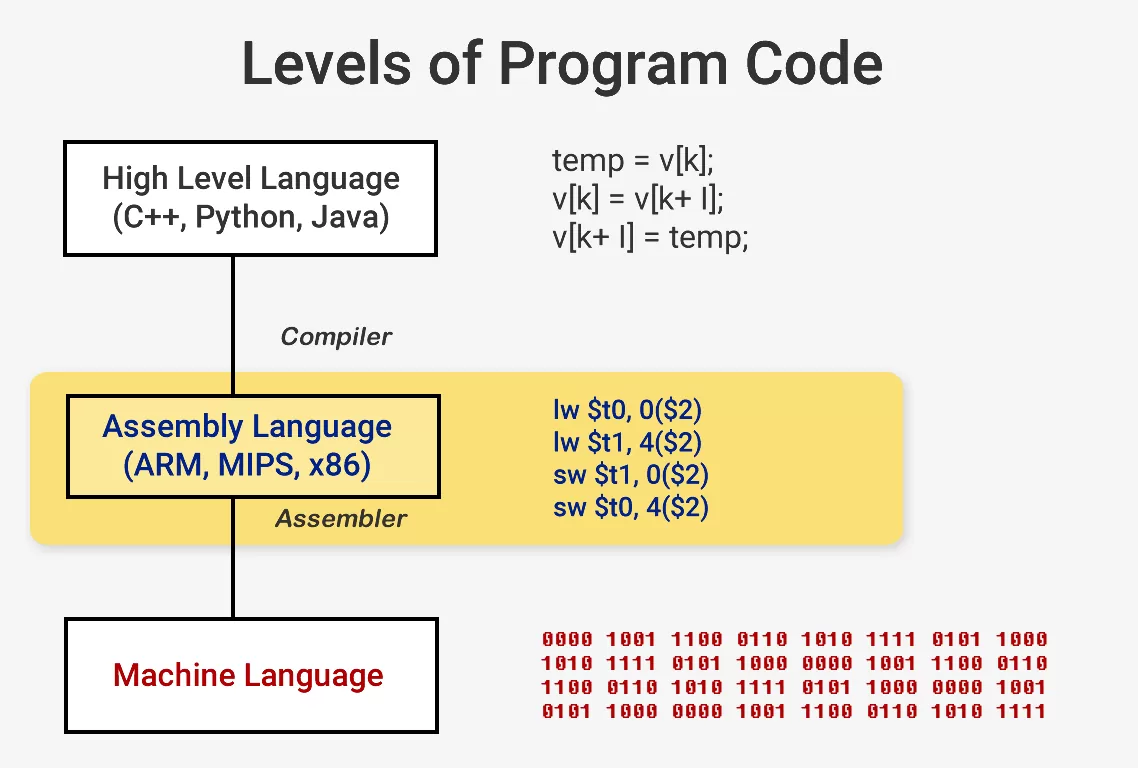
Programs are compiled into a set of low-level instructions chosen assembly linguistic communication as part of an Instruction Set Architecture (ISA). This is the set of instructions that the CPU is congenital to understand and execute. Some of the most common ISAs are x86, MIPS, ARM, RISC-Five, and PowerPC. But like the syntax for writing a function in C++ is different from a function that does the same thing in Python, each ISA has a different syntax.
These ISAs tin can exist cleaved up into two main categories: fixed-length and variable-length. The RISC-V ISA uses fixed-length instructions which ways a certain predefined number of bits in each teaching determine what type of pedagogy it is. This is different from x86 which uses variable length instructions. In x86, instructions tin can exist encoded in dissimilar ways and with unlike numbers of bits for different parts. Because of this complexity, the educational activity decoder in x86 CPUs is typically the most circuitous office of the whole pattern.
Fixed-length instructions permit for easier decoding due to their regular structure, only limit the number of total instructions that an ISA can support. While the common versions of the RISC-Five architecture accept about 100 instructions and are open up-source, x86 is proprietary and nobody really knows how many instructions in that location are. People generally believe in that location are a few thousand x86 instructions but the exact number isn't public. Despite differences among the ISAs, they all acquit substantially the same core functionality.

Now nosotros are ready to turn our reckoner on and offset running stuff. Execution of an didactics actually has several basic parts that are broken down through the many stages of a processor.
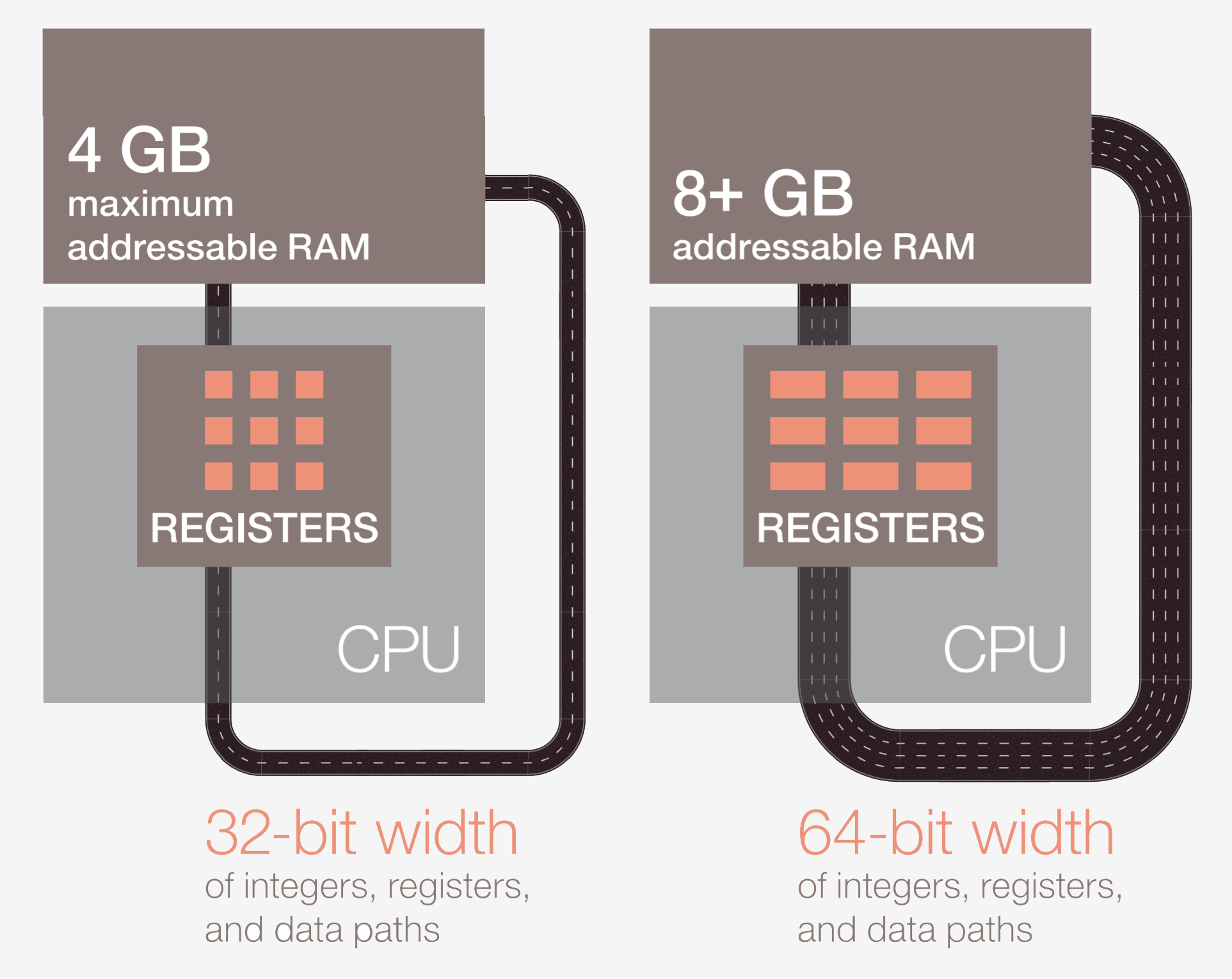
The first stride is to fetch the instruction from memory into the CPU to begin execution. In the second step, the instruction is decoded so the CPU tin can figure out what type of instruction it is. There are many types including arithmetic instructions, branch instructions, and memory instructions. Once the CPU knows what blazon of instruction it is executing, the operands for the instruction are collected from memory or internal registers in the CPU. If you lot want to add number A to number B, you lot can't do the improver until you actually know the values of A and B. Nearly modern processors are 64-bit which means that the size of each data value is 64 bits.
Later the CPU has the operands for the instruction, it moves to the execute stage where the performance is done on the input. This could be calculation the numbers, performing a logical manipulation on the numbers, or but passing the numbers through without modifying them. Later the upshot is calculated, memory may need to be accessed to store the result or the CPU could only go on the value in one of its internal registers. After the result is stored, the CPU will update the country of diverse elements and motion on to the adjacent instruction.
This description is, of grade, a huge simplification and nigh modern processors volition break these few stages up into twenty or more smaller stages to improve efficiency. That means that although the processor will get-go and finish several instructions each bike, it may have twenty or more cycles for any one instruction to consummate from start to terminate. This model is typically called a pipeline since it takes a while to fill the pipeline and for liquid to go fully through it, but once information technology's full, you get a constant output.

The whole bike that an educational activity goes through is a very tightly choreographed process, but non all instructions may finish at the aforementioned fourth dimension. For case, add-on is very fast while partitioning or loading from memory may accept hundreds of cycles. Rather than stalling the entire processor while ane wearisome education finished, most mod processors execute out-of-gild. That means they will decide which instruction would be the most beneficial to execute at a given time and buffer other instructions that aren't ready. If the current instruction isn't set up nonetheless, the processor may bound frontward in the code to meet if anything else is fix.
In addition to out-of-order execution, typical modernistic processors employ what is called a superscalar architecture. This ways that at any one time, the processor is executing many instructions at one time in each stage of the pipeine. It may as well be waiting on hundreds more to begin their execution. In society to be able to execute many instructions at one time, processors will have several copies of each pipeline stage within. If a processor sees that two instructions are gear up to be executed and there is no dependency between them, rather than expect for them to finish separately, it will execute them both at the same time. One mutual implementation of this is called Simultaneous Multithreading (SMT), also known every bit Hyper-Threading. Intel and AMD processors currently back up 2-way SMT while IBM has developed chips that support up to 8-way SMT.

To accomplish this carefully choreographed execution, a processor has many extra elements in add-on to the bones core. There are hundreds of individual modules in a processor that each serve a specific purpose, but we'll merely become over the basics. The two biggest and most benign are the caches and branch predictor. Additional structures that we won't cover include things like reorder buffers, register alias tables, and reservation stations.
The purpose of caches can ofttimes be confusing since they store data just similar RAM or an SSD. What sets caches autonomously though is their access latency and speed. Even though RAM is extremely fast, it is orders of magnitude too tedious for a CPU. Information technology may take hundreds of cycles for RAM to respond with data and the processor would be stuck with nothing to exercise. If the data isn't in the RAM, information technology can have tens of thousands of cycles for data on an SSD to exist accessed. Without caches, our processors would grind to a halt.
Processors typically take three levels of cache that class what is known equally a memory hierarchy. The L1 cache is the smallest and fastest, the L2 is in the middle, and L3 is the largest and slowest of the caches. Higher up the caches in the bureaucracy are small registers that shop a single data value during ciphering. These registers are the fastest storage devices in your arrangement past orders of magnitude. When a compiler transforms high-level program into assembly language, it will make up one's mind the best style to use these registers.
When the CPU requests data from retentivity, it volition first cheque to encounter if that data is already stored in the L1 enshroud. If information technology is, the data tin can be quickly accessed in just a few cycles. If it is not present, the CPU volition check the L2 and later search the L3 cache. The caches are implemented in a fashion that they are generally transparent to the core. The core will but enquire for some information at a specified retention accost and any level in the bureaucracy that has it will reply. As we motility to subsequent stages in the memory hierarchy, the size and latency typically increase past orders of magnitude. At the end, if the CPU can't find the information information technology is looking for in any of the caches, just then will it become to the primary retention (RAM).

On a typical processor, each cadre will have two L1 caches: ane for information and one for instructions. The L1 caches are typically effectually 100 kilobytes total and size may vary depending on the chip and generation. In that location is also typically an L2 cache for each core although it may be shared between 2 cores in some architectures. The L2 caches are usually a few hundred kilobytes. Finally, at that place is a single L3 cache that is shared betwixt all the cores and is on the guild of tens of megabytes.
When a processor is executing code, the instructions and data values that it uses near often will go cached. This significantly speeds up execution since the processor does not have to constantly get to main memory for the data it needs. We volition talk more about how these retention systems are actually implemented in the second and third installment of this series.
As well caches, one of the other key building blocks of a modern processor is an accurate co-operative predictor. Branch instructions are similar to "if" statements for a processor. One set up of instructions will execute if the condition is truthful and another will execute if the condition is fake. For instance, you may want to compare two numbers and if they are equal, execute one function, and if they are dissimilar, execute another function. These branch instructions are extremely mutual and can brand up roughly 20% of all instructions in a program.
On the surface, these branch instructions may not seem like an outcome, but they tin can actually be very challenging for a processor to get correct. Since at any ane time, the CPU may be in the process of executing ten or twenty instructions at one time, it is very important to know which instructions to execute. It may take five cycles to determine if the current instruction is a branch and some other 10 cycles to determine if the condition is true. In that time, the processor may have started executing dozens of additional instructions without even knowing if those were the right instructions to execute.
To get around this result, all modern loftier-performance processors employ a technique called speculation. What this means is that the processor will keep rail of co-operative instructions and gauge as to whether the branch will be taken or not. If the prediction is correct, the processor has already started executing subsequent instructions so this provides a operation gain. If the prediction is wrong, the processor stops execution, removes all incorrect instructions that it has started executing, and starts over from the correct bespeak.
These branch predictors are some of the primeval forms of motorcar learning since the predictor learns the behavior of the branches as it goes. If it predicts incorrectly too many times, it volition brainstorm to learn the right beliefs. Decades of inquiry into co-operative prediction techniques have resulted in accuracies greater than 90% in modernistic processors.
While speculation offers immense performance gains since the processor can execute instructions that are ready instead of waiting in line on busy ones, it also exposes security vulnerabilities. The famous Spectre attack exploits bugs in co-operative prediction and speculation. The aggressor would use specially crafted code to go the processor to speculatively execute lawmaking that would leak retentiveness values. Some aspects of speculation have had to be redesigned to ensure data could not exist leaked and this resulted in a slight drop in performance.
The architecture used in modern processors has come a long way in the by few decades. Innovations and clever design have resulted in more performance and a amend utilization of the underlying hardware. CPU makers are very secretive most the technologies in their processors though, so it'south impossible to know exactly what goes on inside. With that beingness said, the fundamentals of how computers work are standardized beyond all processors. Intel may add together their secret sauce to boost cache hit rates or AMD may add together an advanced branch predictor, but they both attain the aforementioned task.
This outset-await and overview covered most of the basics nearly how processors piece of work. In the second part, we'll discuss how the components that go into CPU are designed, cover logic gates, clocking, power direction, circuit schematics, and more.
This article was originally published in April 22, 2022. We've slightly revised information technology and bumped information technology equally role of our #ThrowbackThursday initiative. Masthead credit: Electronic circuit board close upwards by Raimudas
Source: https://www.techspot.com/article/1821-how-cpus-are-designed-and-built/
Posted by: delanosamid1984.blogspot.com


0 Response to "How CPUs are Designed and Built"
Post a Comment